As the cryptocurrency industry develops and digital assets gain popularity, more and more users worldwide are encountering fraudulent schemes. Cybercriminals are constantly refining their methods, and even experienced investors can fall victim to their elaborate schemes. Participating in dubious projects can be very costly: at best, you'll lose your investment; at worst, you risk losing all your funds. In this review, we'll explain how to avoid such problems and what measures can help protect you from scammers.
Content:
- What is a cryptocurrency scam?
- Factors influencing fraudulent activity
- Types of cryptocurrency scams
- Popular schemes and how they work
- How to check a project and token before investing
- How to protect your crypto wallet
- General principles of security in the cryptocurrency sphere
- Conclusion
What is a Cryptocurrency Scam?
The term "scam" comes from the English language—the word "scam" translates as "fraud" or "deception." It refers to any fraudulent scheme involving digital assets: cryptocurrencies , tokens, and NFTs . Fraudsters most often target users' personal data, private keys, and funds.
The Difference Between Scam, Fraud, and Phishing
|
Term |
Scope of application |
How it is done |
|
Scam |
It is a method of coercing the victim into making a transaction or voluntarily revealing confidential information. |
The victim transfers money, purchases a token, or sends a key, relying on deceptive promises of high profits. |
|
Fraud |
Using stolen information without the owner's permission. |
Fraudsters use stolen victim data to conduct secret financial transactions. |
|
Phishing |
A specific method of committing a scam or fraud. |
Scammers pretend to be a trusted source to trick users into revealing their logins and private keys. |
Why is Cryptocurrency so Attractive to Scammers?
Cryptocurrencies attract fraudsters for a number of reasons, primarily because of the anonymity and irreversibility of transactions. Unlike traditional payment systems like Visa and Mastercard, where a transaction can be reversed or at least blocked upon the victim's request, cryptocurrency transactions cannot be reversed due to the nature of blockchain technology.
All transactions are permanently recorded in blocks protected by a unique digital fingerprint—a hash. Each new block contains the hash of the previous one, forming a sequential chain: attempting to change even one entry will change the hash of the corresponding block and require recalculating all subsequent hashes, which is impossible in practice.
In addition to irreversibility, scammers exploit the pseudo-anonymity of cryptocurrencies: despite the transparency of the blockchain (all transactions are visible), the wallet address is not directly linked to a person's passport information, facilitating money laundering and quick transfers between accounts.
Finally, creating counterfeit assets and services is also extremely simple: a fake token can differ from a popular one by just one letter, and it's similarly easy to create a fake website or app.
Factors Influencing Fraudulent Activity

If you're investing in cryptocurrencies, you should always exercise caution. However, there are periods when scammer activity is at its peak. This is especially true during bull markets. During these periods, a huge number of Ponzi schemes, scam projects, and fake ICOs and NFTs emerge.
Why is a bull market especially dangerous? During this period, many investors experience a fear of missing out—FOMO. They unconditionally believe in the success of any project, even a dubious one, without bothering to verify it. The key is not to miss out on the "next Bitcoin."
Furthermore, many newcomers are entering the market, buoyed by news of cryptocurrency's astonishing returns. These newcomers are unfamiliar with the basics of security and blockchain operation. These investors become ideal targets for scammers.
When the cryptocurrency market is in a bearish phase , malicious activity decreases but becomes more targeted. Cybercriminals rely on phishing and account hacking, preying on remaining assets and offering "fund recovery services" or a "guaranteed solution to the crisis."
Fraudster activity is influenced not only by changing trends , but also by the launch of new technologies and the emergence of tokens from well-known global brands. The former allow attackers to create fake protocols and exploit vulnerabilities in new smart contracts, while the latter enable the creation of fake apps or phishing sites that mimic the interfaces of new protocols.
Types of Cryptocurrency Scams
Cryptocurrency scams are constantly evolving. New financial schemes and blockchain attack methods appear on the market every year. Below are the most common ones.
Phishing and Fake Websites/Apps
 Phishing involves creating exact copies of legitimate services. Fraudsters send victims emails or SMS messages with a link to a fake page. By clicking the link, the user enters their login credentials or seed phrase, and the scammers gain access to their funds.
Phishing involves creating exact copies of legitimate services. Fraudsters send victims emails or SMS messages with a link to a fake page. By clicking the link, the user enters their login credentials or seed phrase, and the scammers gain access to their funds.
Rug Pull (Scam Projects) 
In this method, scammers create a new token — usually a memecoin or DeFi project — and aggressively promote it on social media in an attempt to attract investors.
Once a project gains popularity and attracts significant investment, attackers drain all liquidity. The token's price instantly drops to zero, and the affected investors are unable to sell it due to a lack of buyers. Such schemes are most commonly used on decentralized exchanges and in new DeFi projects.
Pump & Dump Diagrams
 In this popular cryptocurrency scam, a group of criminals buys a large amount of a little-known token and then pumps its price through mass advertising.
In this popular cryptocurrency scam, a group of criminals buys a large amount of a little-known token and then pumps its price through mass advertising.
When the price peaks, scammers begin selling their coins en masse (dumping), causing the price to plummet. Such schemes are actively spread through social media groups and messaging apps.
NFT Scams 
The idea behind this scheme is simple: attackers raise funds to issue a new token or NFT collection.
To do this, they create websites with attractive, professional designs that talk about the supposedly existing project "roadmap," the team members, and the product, supposedly aimed at a sought-after market.
As you might guess, after collecting the required amount and selling the entire collection (mint), the scammers disappear with the investors' money, without fulfilling a single promise.
Popular Schemes and How They Work
There are many ways to scam the cryptocurrency market, but pseudo-arbitrage and pseudo-tokens have recently become particularly popular.
Pseudo-arbitration
This is a fraudulent scheme masquerading as genuine cryptocurrency arbitrage. This is precisely the danger: it looks like legitimate deals and can deceive even an experienced investor.
First, let's understand what arbitrage is. Classic cryptocurrency arbitrage is the exploitation of price differences for the same asset across different trading platforms to generate profit. An investor buys a coin at a lower price on one exchange and sells it at a higher price on another, profiting from the price difference.
In pseudo-arbitration, attackers use this approach as a cover, but it works entirely differently. The entire process consists of four stages:
- Baiting the victim. Fraudsters spread information about a supposedly "guaranteed" and "safe" way to profit from exchange rate fluctuations. However, such claims appear overly simplistic and unrealistically profitable.
- Promising the Impossible. Often, the scheme is based on the manipulative claim that cryptocurrency can be transferred between completely different and technologically incompatible blockchains. For example, they might promise "exclusive access to a bridge" between networks, which in reality doesn't exist and cannot exist due to the significant differences in the technologies used.
- The illusion of the method's effectiveness. At this stage, the victim is shown that the proposed scheme works. They are usually asked to transfer a small amount "as a test" to ensure its effectiveness.
- The final step is the loss of funds. At the final stage, when the victim is convinced that the method supposedly works and transfers a large sum, the scammers either disappear with the money, or the transaction "unexpectedly gets stuck" in the depths of a non-existent "bridge" due to technical problems.
The main sign of a scam: in a pseudo-arbitrage scheme, scammers trick victims into transferring funds to unknown third-party platforms, platforms, or wallets, supposedly to transfer or exchange at a particularly favorable rate. Never trust offers that attempt to circumvent basic and market restrictions.
Pseudotokens
This is another dangerous and widespread type of scam. In this scheme, criminals exploit the ease of creating new digital assets on the blockchain. Pseudotokens are counterfeit cryptocurrencies that closely resemble popular, real-world coins such as USDT , USDC, ETH , and others in appearance and name, but have no real value and are created solely for deception.
The fact is that creating a new token on the blockchain network is cheap and easy. Virtually anyone can issue a token and give it any name or symbol (for example, $USDC, $Tether, $ETH). Fraudsters give their fake tokens names similar to popular assets. For example, they might issue a token called USDC, but on the blockchain, such a token would be called "USDC Real" or "USDC Coin v2.0."
It goes without saying that such fake tokens are not backed by anything, and their value is zero.
There are three main schemes for using pseudo-tokens:
- Address poisoning is sending funds to a scammer's address that is very similar to yours.
- Fake airdrops are offers to "receive" tokens with a fake name (e.g. UNI or ETH) and sign a malicious transaction.
- "Honeypot" - blocking the ability to sell tokens for everyone except the creator of the pseudo-token.
How to Check a Project and Token Before Investing
There are a few simple rules to follow before deciding to invest in a new token:
- Pay attention to the contract address – each real token has a single official smart contract address on a specific blockchain.
- Verify the address only using official sources: CoinMarketCap, CoinGecko, or the project's official website. Compare it with the address in your wallet or on the exchange.
- Never rely solely on the name and symbol - they are easily counterfeited.
- Pay attention to trading activity – pseudo-tokens usually have minimal transaction history and are not listed on major centralized exchanges (Binance, Coinbase, ByBit, etc.).
Honeypot Detector
Many scam projects employ a scheme whereby only the owner of the smart contract can sell tokens. How does this work in practice? It's quite simple: you buy an asset, for example, through Uniswap or PancakeSwap, and add it to your wallet. Initially, you watch its value rise: you invest $1,000, and the next day the "paper" amount has increased to $2,000, then to $3,000 or even $4,000.
A month later, you're already showing $20,000. It seems like you've hit the jackpot. But as soon as you try to sell the asset, nothing happens. The reason is simple: the smart contract has a restriction: the sell function can only be used by its owner, and is blocked for everyone else.
The Honeypot Detector service helps avoid such traps. It simulates purchase and sale transactions for a given token and determines whether it is a honey trap. Most such scams operate on the BNB Chain network due to the low cost and ease of issuing smart contracts.
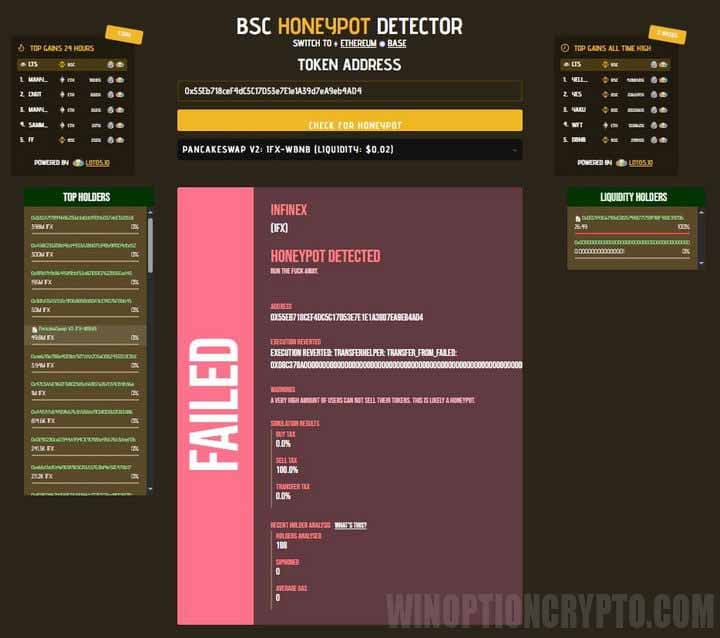
To verify an asset, simply enter its smart contract address in the service's search bar and click "Check." If the system displays a red "FAILED" warning and a message like "Run the fuck away," this is a clear sign of a scam.
Token Sniffer
Another useful tool for token verification is the Token Sniffer service. Unlike Honeypot Detector, it supports smart contract analysis across multiple networks, not just the BNB Chain.
Token Sniffer operates similarly to Honeypot Detector: enter the smart contract address, and the service will automatically test it and provide a final reliability rating.
CERTIFIED
Another useful resource for checking assets is CERTIFIED. This website provides ratings of cryptocurrencies, wallets, and various tokens. Here you can find out whether a specific token or trading platform has been audited and view its rating. The most important indicator is its position in the list. If the asset you're interested in is near the bottom of the rating, it's best to refrain from purchasing it.
CryptoScamDB Scam Project Database
It's a good idea to check the project you're interested in against the extensive cryptocurrency scam database. At the time of writing, it contained information on over 9,000 fraudulent projects. If you come across a "super-profitable" investment offer in a crypto project, be sure to check it against this database. This simple check can save you from losing a significant portion or even all of your capital.
Smart Contract Analysis with Etherscan and BscScan
In addition to the services listed above, be sure to check the project in specialized "search engines" for the relevant blockchains—analytics tools like Etherscan and BscScan. These seemingly similar resources provide access to public blockchain data in real time.
Regardless of the platform chosen, they perform the same basic functions:
- Transaction tracking – searching by hash (TXID) allows you to determine the transaction status (successful, pending, canceled), time, amount, sender and recipient, as well as the fee (Gas Fee).
- Wallet and address analysis – by entering a public address, you can check the current balance of its native token (ETH, BNB), the history of all transactions, and a list of ERC-20 and BEP-20 tokens located in this wallet.
Overall, Etherscan and BscScan are useful tools for any decentralized finance (DeFi) user, as they can be used to verify any transactions on their respective blockchains.
How to Protect Your Crypto Wallet
The number of phishing attacks, scam projects, and smart contract hacks increases every year. Therefore, to protect your crypto assets, it's important to adhere to basic digital security rules and use modern tools to combat fraud.
Using Pocket Universe
Most cryptocurrency holders use Metamask or Trust Wallet. If you use Metamask as a browser extension, we highly recommend installing Pocket Universe, a dedicated Web3 security extension. Its primary purpose is to protect your assets from phishing and malicious smart contracts. Essentially, Pocket Universe can be considered an antivirus for your Web3 transactions.
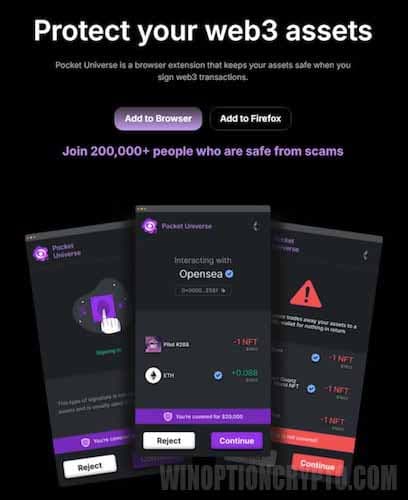
It's crucial to understand: installing Pocket Universe will warn you the moment you're about to sign a dangerous smart contract. The extension will show you that signing it gives attackers full access to your wallet funds. Without this protection, you simply won't notice and risk losing all your assets.
Hardware Wallets (Ledger, Trezor)
One of the key ways to protect crypto assets is to store them in hardware (cold) wallets that are not connected to the internet. This keeps private keys out of the reach of hackers, making them virtually invulnerable to attacks and hacking.
Comparison of Ledger and Trezor wallets
|
Parameter |
Ledger |
Trezor |
|
Safety principle |
A proprietary development based on the Secure Element chip. It offers a level of security similar to bank cards. |
Open source software available for audit by the crypto community. |
|
Convenience |
Supports Bluetooth for communication with mobile devices. |
The Trezor T model has a color touch screen. |
|
Supported assets |
Over 5,500 cryptocurrencies, including staking and NFTs. |
Lots of cryptocurrencies, but less than Ledger. |
|
Models |
Ledger Nano S Plus, Nano X (with Bluetooth), Stax (premium with a large screen). |
Trezer One (buttons), Model T (touchscreen), Safe ⅗ |
Multi-signatures and Backups
For increased security, use multi-signature and backups. Unlike a regular wallet, a multi-signature wallet works like a safe with multiple locks: multiple signatures are required to transfer funds. This approach protects your assets—if lost, compromised, or hacked, a single signature won't be enough to complete a transaction.
It's important to understand that in the crypto industry, backups aren't just a copy of your data; they're the only way to protect your savings in case of a problem. Unlike a regular bank, where you can reissue a card and block the old one, losing a physical backup will result in the loss of your entire capital. Therefore, be sure to use seed phrases to restore all private keys.
Be Careful with Airdrops and dApps
Airdrops and decentralized applications (dApps) offer good investment opportunities, but they also pose major pitfalls for unwary users. Beginners should ignore unfamiliar tokens and only trust airdrop links from official project channels on X, Discord, and official websites. Furthermore, use a separate wallet with a minimum amount of funds to participate in the airdrop.
When working with a dApp, before connecting your wallet, ensure that the website address matches the official app address. If possible, limit the amount you allow to interact with the dApp, and regularly check which contracts and tokens you've granted permissions to using analytics services like Etherscan and BscScan. Don't forget to revoke outdated and unnecessary permissions.
General Principles of Security in the Cryptocurrency Sphere
Now, a few words about the basics of cryptocurrency security that all users, from beginners to professionals, should adhere to.
Storing Seed Phrases Offline
Never, under any circumstances, store your seed phrases electronically: not on your computer, not in cloud storage, not even as a photo on your phone. Any digital storage makes them vulnerable to theft — this is precisely the kind of data hackers are after. Security experts recommend storing seed phrases on physical, fire-resistant media, as regular paper can rot or burn. The most reliable option is engraving on a steel plate, which guarantees the safety of your assets even in the event of a system failure or fire.
Two-factor Authentication
If a seed phrase is the key to your safe, then two-factor authentication (2FA) is the alarm system that guards access. It adds a critical second layer of security: even if attackers steal your password, they won't be able to log in without a second unique code generated by your smartphone or other device.
For maximum security, use authenticator apps (such as Google Authenticator) rather than SMS, which can be easily intercepted.
Checking Links and Sources of Information
Fraud in the crypto industry thrives primarily through phishing, social engineering, and disguise as legitimate projects. Therefore, your primary weapon should be thorough verification of all sources. Before clicking an airdrop link or connecting a wallet to a dApp, always verify the URL against the project's official channels on X, Discord, and CoinGecko.
Remember: fraudulent websites often differ by just one character in the address. Never trust personal messages or emails that demand urgent action or offer "free" tokens. Legitimate projects publish such information only on their official websites and social media pages.
Checklist: What to Do Before Investing
- Make sure the smart contract you choose has been audited by independent security companies (CertiK, PeckShield, Hacken). A lack of audit is a serious red flag.
- Study how tokens are distributed. If one or more wallets control more than 10-15% of the tokens, this indicates a potential pump-and-dump risk.
- Check out the development team: who they are, whether they are public figures, whether they have a LinkedIn profile.
- Review the project roadmap. Assess how realistic and specific the plans are.
- Analyze community activity in the project's official channels on Discord, Telegram, and X. If there are no real discussions in the public channels, but rather spam and bots, abandon the project.
- Assess how the team responds to feedback from real users. Openness is a good sign and a sign of the project's reliability.
- Determine your risk level. Invest only the amount you're willing to lose, and use a separate wallet for your investments, separate from your main account.
Conclusion
In this review, we've examined the most common cryptocurrency scams and provided recommendations to significantly reduce your risk of becoming a victim. However, keep in mind: scammers are constantly developing new ways to steal your funds. Be vigilant and always be skeptical of any "tempting" offers.




To leave a comment, you must register or log in to your account.